Vulnerability Management
Cloyt Security’s Vulnerability Management solution helps you detect weaknesses before they become threats. Prioritize risks, streamline remediation, and safeguard your digital environment with continuous, actionable insights.

Our Vulnerability Management Services
Cloyt Security provides comprehensive vulnerability management to protect your business from evolving cyber threats. Our services include continuous scanning, risk assessment, prioritization, and remediation guidance, ensuring that vulnerabilities are identified and addressed before they can be exploited. With actionable insights and expert support, we help you strengthen your security posture and maintain compliance with industry standards.
Infrastructure VM
We safeguard your core IT infrastructure with end-to-end vulnerability management. We continuously scan servers, networks, databases, and cloud environments to uncover hidden risks. Our experts prioritize vulnerabilities based on real-world threat impact and provide clear remediation guidance, ensuring your infrastructure stays resilient, compliant, and secure against evolving cyberattacks.
Application VM
Our service identifies vulnerabilities across web, mobile, and enterprise applications, from insecure code to misconfigurations. We provide continuous testing, risk-based prioritization, and expert remediation support—ensuring your applications remain resilient against exploitation while meeting compliance and industry best practices.
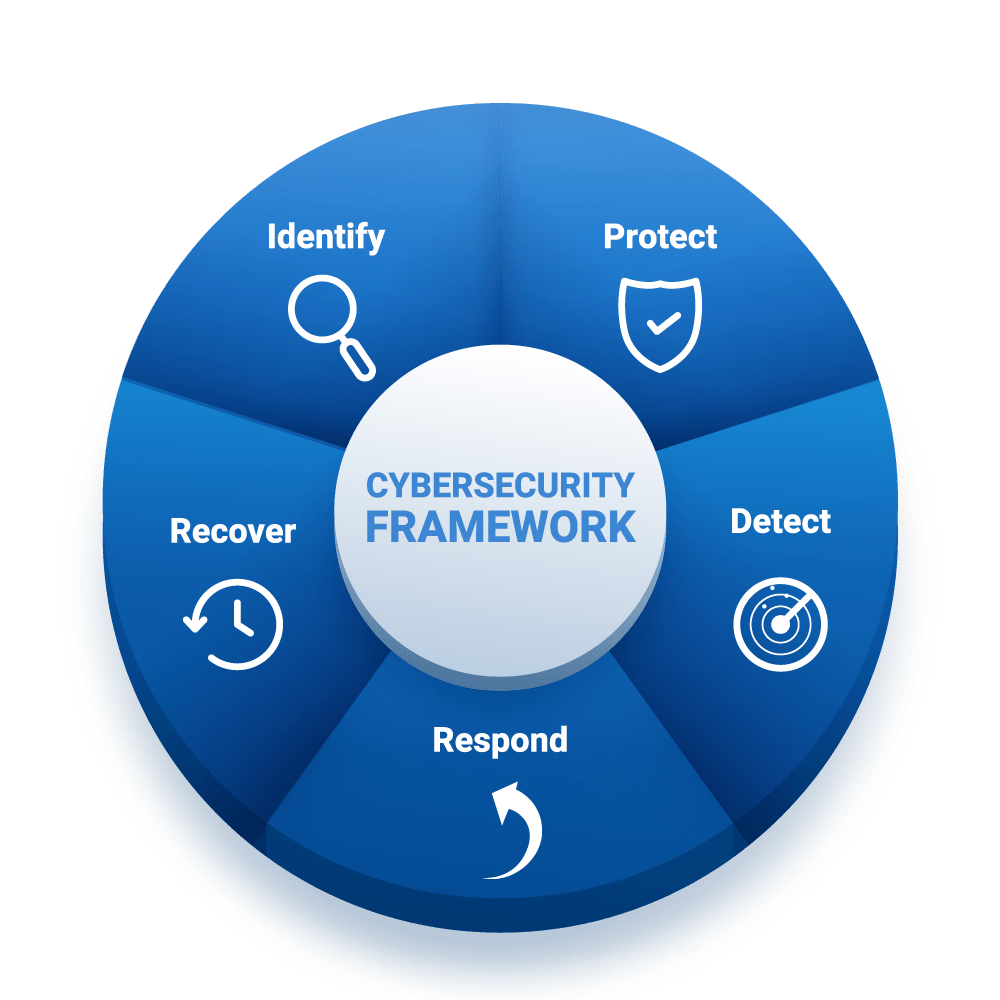
How It Works
We make vulnerability management simple, transparent, and effective:
Discover – We scan your applications, systems, and endpoints to uncover hidden vulnerabilities.
Assess – Risks are analyzed and prioritized based on severity and business impact.
Remediate – Our experts guide you through fixing weaknesses with practical, step-by-step recommendations.
Validate – We retest to confirm issues are resolved and no new risks remain.
Monitor – Continuous monitoring ensures you stay protected against emerging threats.
Infrastructure Vulnerability Management
Your infrastructure is the backbone of your business — from servers and networks to cloud platforms and connected devices. Weaknesses in these systems create entry points for attackers. Cloyt Security’s Infrastructure Vulnerability Management helps you identify, prioritize, and remediate risks across all critical assets.
What We Cover
-
Network Assets: Firewalls, routers, switches, and wireless networks tested for misconfigurations and exposures.
-
Servers & Endpoints: Windows, Linux, and macOS systems scanned for unpatched vulnerabilities, outdated software, and insecure settings.
-
Cloud Environments: AWS, Azure, Google Cloud, and hybrid infrastructures reviewed for misconfigurations, identity & access risks, and compliance gaps.
-
Databases & Storage: Validation of permissions, encryption, patch levels, and access controls to secure sensitive data.
-
Virtualization & Containers: Assessments of VMware, Kubernetes, and Docker environments for image vulnerabilities and runtime risks.
-
IoT & Connected Devices: Identifying unmanaged assets and securing endpoints that often fall outside traditional defenses.
How we deliver
Discovery & Mapping – We identify all infrastructure assets, on-premises and in the cloud.
Vulnerability Scanning & Testing – Automated tools plus expert validation to uncover risks.
Risk Prioritization – Issues ranked by severity and business impact, so you know what to fix first.
Remediation Guidance – Clear, practical steps for patching, configuration changes, or policy updates.
Continuous Monitoring – Ongoing scans and reporting to keep you ahead of emerging threats.
With Cloyt Security, you gain full visibility across your infrastructure, reduce attack surfaces, and ensure your business-critical systems stay secure and compliant.
Application Vulnerability Management
Your applications are often the front door to your business — and a prime target for attackers. Cloyt Security’s Application Vulnerability Management helps you identify, assess, and remediate weaknesses in web, mobile, and enterprise applications before they can be exploited.
What We Cover
- Web Applications: Testing for OWASP Top 10 risks like SQL injection, XSS, CSRF, and authentication flaws.
- Mobile Apps: Security reviews of iOS and Android applications for insecure storage, data leakage, and API vulnerabilities.
- APIs & Microservices: Validation of access controls, encryption, and data handling across modern architectures.
- Enterprise Applications: Assessments of ERP, CRM, and SaaS tools for misconfigurations and insecure integrations.
- Secure SDLC Integration: Embedding security testing into development pipelines (DevSecOps) for early detection.
How we deliver
Discovery & Mapping – Identifying applications, APIs, and critical data flows.
Vulnerability Testing – Automated scanning with tools and validated by manual expert testing.
Risk Prioritization – Ranking vulnerabilities by severity and potential business impact.
Remediation Guidance – Actionable fixes for developers and IT teams, aligned with secure coding practices.
Continuous Protection – Ongoing testing and monitoring to secure updates, releases, and third-party integrations.
With Cloyt Security, you can release applications with confidence, reduce development risks, and protect both your business and your customers from evolving threats.
Contact Us
info@cloytsecurity.com
1 Marina Park Drive Suite 1230, Boston, MA 02210, United States
Monday-Friday: 8am - 5pm
Get Started
Defend Your Business from Cyber Threats
